Cybersecurity Primer
A primer on the cybersecurity industry
This is the fourth primer in a series of primers I’ll be writing over the next 6-12 months. You can find the other three here (and I hope they’re increasing in quality as I write more of them):
I have a broader goal to write a primer for each of the major industries in tech to provide a complete picture of the tech ecosystem. I like to make it clear that I’m not a cybersecurity expert. I will certainly make mistakes; my goal of these articles is to gain a ‘0 to 1’ understanding of these industries and hopefully provide readers with the same understanding.
An important disclaimer: The cybersecurity industry is exceptionally fragmented, quite complex, and I’m admittedly a beginner in the space. For more security-related information, Strategy of Security and The Software Analyst Newsletter are two excellent resources.
Here’s how the article will be structured:
Intro to Cybersecurity & Key Concepts
Brief History of Cybersecurity
Overview of Cybersecurity Landscape
Security Segments
Edge Security
Network Security
Cloud Security
Data Security
Infrastructure Security
Security Operations
Where The Major Players Fit In
Cybersecurity Basics
At its core, cybersecurity is about protecting an individual’s or company’s resources (data, digital assets, physical assets) from cyber threats. Those threats can include malware (software threats), ransomware (malware that locks/encrypts data), DDoS attacks (overwhelming a system), phishing (sending emails/messages to trick users), among other threats. These threats can be introduced through devices, software, physical infrastructure, or user accounts.
The goal of cybersecurity is to prevent those attacks from occurring (prevention), find when those attacks do occur (detection), and remediate those threats once they’re known (response). This needs to be done across the tech stack from devices to networks, to cloud environments, to physical infrastructure.
Some basic background on networks:
Devices are connected locally to a switch in a Local Area Network (LAN). A router then connects to other LANs creating a Wide Area Network (WAN). This then will connect to internet service providers and the cloud. These networks can be in homes, offices, data centers, etc. Traditionally, cybersecurity was a castle-and-moat architecture. The goal was to keep bad guys out of the “protected network” using technologies like a software/hardware firewall at the router/switch level.
Now, the “Zero-Trust” methodology assumes that no device or network is safe. Companies use “defense-in-depth” methods to have many layers of defense. If one layer of defense is compromised (a firewall for example), a threat will have to face other security measures (other firewalls, encryption, access security, cloud security, software security, physical security) to get access to protected resources.
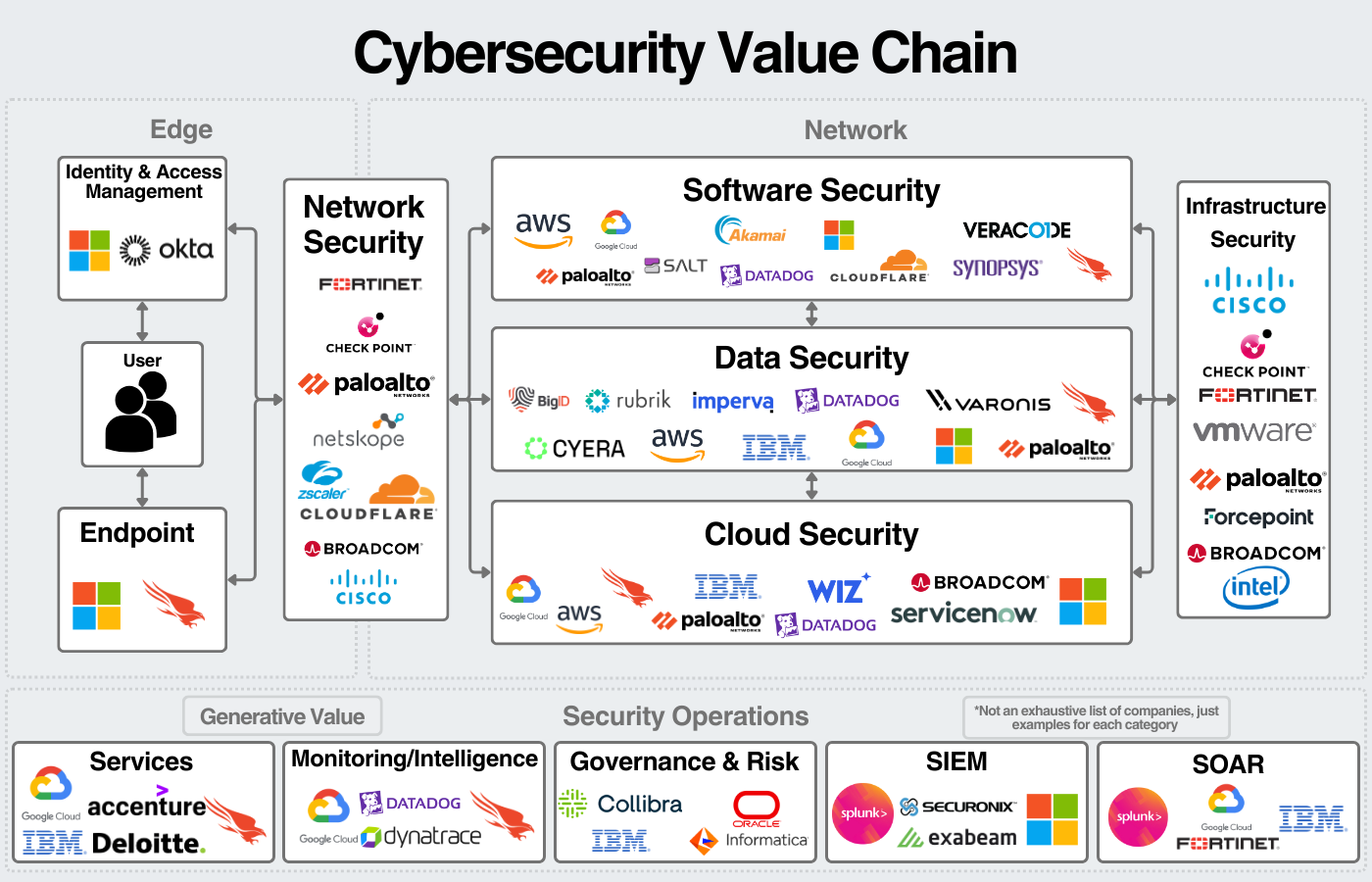
If we visualize (at a high level) what this looks like, we can get a decent mental model like this:
The key point with this graphic is that these are not black & white boundaries. Since data is constantly being exchanged between these segments, they have to be tightly integrated to create a secure environment.
History of Cybersecurity
I think it’s valuable to look at the history of the industry to understand it from a fundamental level. Cybersecurity has evolved with technology over the last 50 years. As technology continued to advance, so did the threats with that technology. Cybersecurity was the solution to those threats.
The Pre-Internet Era (1970s)
Networking has always been closely tied to security, so it’s a good place to start. ARPANET was one of the early computer networks. Researcher Rob Thomas wrote a program called Creeper that would move from computer to computer leaving the note “I’m the creeper, catch me if you can!” This was one of the early examples of how computer viruses could develop. Ray Tomlinson, the inventor of email, wrote the program called Reaper which eventually chased and deleted Creeper. This was the first example of an antivirus.
These early examples painted the picture of how cybersecurity would evolve with technology. Tech would be invented, threats would emerge, and cybersecurity would find ways to protect that technology. The industry would start to see commercialization in the 1980s.
The Early Internet Era (1980-1990s)
The 1980s saw the dawn of the cybersecurity industry. In 1987, the first commercial antivirus was introduced by a few companies around the same time. McAfee was one of those early companies and would maintain its competitive position for the coming decades. 1989 saw the emergence of one of the first firewalls from DEC (Digital Equipment Corporation), providing organizations with a way to safeguard their networks. However, it lacked the necessary technology to fully protect networks. In 1993, Checkpoint Security was founded as one of the early stateful firewall (a firewall that tracks and monitors the state of networks, instead of just analyzing information when it passes through the firewall) companies.
As the Internet became widespread, the associated vulnerabilities became more clear leading to innovations in the modern Internet era.
The Modern Internet Era (2000s-Today)
We can break down the modern cybersecurity era into pre-cloud and post-cloud cybersecurity. We’ll make a rather large jump here with technology; as technology exploded after the dot-com bubble, each new technology needed to be secured.
In the early 2000s, we saw a new generation of firewalls from current industry giants like Fortinet (founded in 2000) and Palo Alto Networks (founded in 2005). These firewalls provided greater insight into how applications were communicating over the network and provided more control over how information could pass through a network. For more on Palo Alto’s story, this is a great article.
As the amount of enterprise data grew, tools like Splunk (founded in 2003) became popular to track a company’s assets and identify when security threats emerged.
The cloud significantly lowered the barrier of entry to developing software, leading to a new breed of security companies. Zscaler was founded in 2007, Datadog in 2010, and Crowdstrike in 2011; among hundreds/thousands of other cloud-based software providers. Identity and Access Management also further developed in the cloud era with Okta founded in 2009.
As mobile devices became prevalent, endpoint security became a larger priority. Crowdstrike was founded in 2011. Gartner first coined the term Endpoint Threat Detection & Response in 2013.
Over the next decade, new cloud-based security companies continued to be founded. Additionally, big tech companies entered the security realm in addition to the expansion of companies like Palo Alto and Crowdstrike into platforms.
Let’s get back to the original goal of cybersecurity: protect people and organizations’ tech assets from threats. As more data, more tools, and more threats emerged; cybersecurity had to keep up. This brings us to today with an incredibly fragmented industry, intense competition, and the increasing complexity of cyberattacks.
Overview of Cybersecurity Landscape
Because of how fragmented the security space is, simplifying it into one graphic is challenging. I had to make two concessions:
I had to use some acronyms in the graphic; I’ll spell them out when I cover the specific technologies.
Inevitably, I left out some important technologies and companies. I appreciate that if you’re reading this, you likely understand the nuance of studying industries.
The last note is that this is my mental model for the industry (as a relatively new student of the security space). This model makes sense to me, it may not to everyone.
I view the industry in three areas: edge security, network security, and security operations. Edge meaning the users and the technologies directly in use by those users. For the most part, I see this as the “perimeter”. Network refers to the “protected” connected resources within an organization’s network. The network connects the majority of a company’s data, applications, and infrastructure; network security is aimed at protecting those resources from threats.
Finally, we have lifecycle technologies that I’m referring to as “security operations”. These are the processes that go on throughout the lifecycle of security. These technologies & services are responsible for preventing, analyzing, and responding to threats across an organization’s assets.
Security Segments
1. Edge Security - Protecting Users & their Platforms
The edge, as I’m calling it, refers to the perimeter of an organizations’ assets. This includes the users, the devices they use, and the technologies to determine if/how users can access the network. Identity & Access Management (IAM) and Endpoint Security are the two major segments in the edge category.
Identity & Access Management
Identity & access management (IAM) is the process of identifying who someone is and what they have access to. Some security experts consider “identity as the new perimeter”.
A typical IAM system will consist of a database of users, that database will store data on what users are in an organization and what permissions they have. Four main components make up the IAM space: authentication & authorization, identity lifecycle management, access control, and identity governance.
The key point to understand is that identity and access management allows companies to determine who can access the network and what they should have access to.
The IAM space is quite competitive with large software companies (Microsoft, GCP, AWS, Oracle) offering IAM services in addition to vendors like PingIdentity and Okta offering IAM services.
Endpoint Security
Endpoint security ensures that users have a trusted platform to access the network. Everything done in the IAM space depends on having a trusted platform that it’s coming from. An endpoint refers to every business and personal device that can be at the edge such as phones, desktops, laptops, and even IoT devices. All of these contribute to a company’s attack surface.

Endpoint systems are managed through a central endpoint management system, a single console to apply policies across all devices. Endpoint security then has a few competencies: prevention, detection, and response.
Antiviruses prevent known malware and find new threats. Endpoint Detection & Response (EDR) tools continuously monitor devices to detect and respond to threats. They do this by tracking data on each endpoint, filtering that up to a central database, and analyzing for anomalies. Extended detection & response (XDR) is the next evolution of EDR. XDR centralizes all of an organization’s security data from endpoints, networks, and cloud environments to identify potential threats.
Crowdstrike and Microsoft are the two largest vendors in the endpoint security market. SentinelOne, Palo Alto Networks, Trellix, Trend Micro, and VMware are other competitors.
2. Network Security - Protecting the Exchange of Data in the “Trusted” Network
Traditionally, cybersecurity was a castle and moat architecture - i.e. keep the bad guys out of the castle and you’ll be fine. However, as technologies have become more complex and distributed, network security has expanded as well. At its core, networking is the way to transfer data between devices. The “network” in the context of cybersecurity is a company’s network of connected devices. This includes data centers, cloud environments, applications, offices, and data.

Network security is protecting the transfer of data into that network and data being transferred within the network. Some of the major technologies include firewalls, intrusion detection & prevention systems, virtual private networks, secure web gateways, and secure access service edge (SASE).
Firewalls inspect traffic as it enters/exits the network, and can be hardware or software firewalls. Their core technology is packet inspection, where the firewall will inspect where data is coming from and where it’s going. Advanced firewalls can monitor traffic patterns and apply several additional controls to secure networks. Market leaders include Palo Alto Networks, Fortinet, and Check Point.
An Intrusion Detection System (IDS) sits behind the firewall, and further inspects network traffic. An IDPS takes this one level further and will automatically respond to network attacks. Market Leaders include Cisco, TrendMicro, and McAfee.
Secure Web Gateways act as an intermediary between a company’s users and the internet. They aim to protect users from unsafe web content. They do this through URL filtering, anti-malware detection, and application control. Market Leaders include Zscaler and Symantec.
Finally, Secure Access Service Edge (SASE - pronounced Sassy) aims to integrate networking + security and deliver it over the cloud. At its core, it aims to provide a secure way to access the internet, cloud, and applications. Using some of the technologies listed above provides a secure way for users to access resources.
The important thing to keep in mind with networks is that they’re not an abstract concept. Networks physically and digitally connect resources; network security is about protecting the transfer of data between those resources.
3. Cloud Security - Protecting Cloud Environments
Cloud security is a collection of tools aimed at protecting cloud infrastructure, applications, and data. Cloud security is not a standalone segment as it is concerned with protecting networks in the cloud, applications in the cloud, and data in the cloud.
Some quick background on the model for cloud security.
The responsibility for security depends on the model of deployment. The cloud providers always manage physical security while the customer always manages edge security. The intermediary layers typically are a joint effort with cloud providers offering native security tools in their products with the assumption that customers should take additional measures to secure their environments.
Several tools are used to protect cloud environments, and we’re seeing cloud security platforms become prevalent. Cloud Access Security Brokers (CASB) act as another layer of defense before a user can access a cloud environment. It manages authentication, authorization, and data governance/security for users accessing cloud environments.
A Cloud Workload Protection Platform (CWPP) is a unified security platform for monitoring and detection of cloud workloads. It focuses on runtime protection (protection once an app is in production) and vulnerability management. Cloud Security Posture Management (CSPM) aims to identify misconfigurations in cloud environments that could lead to security breaches.
Several other tools exist to secure specific workloads such as containers, Gen AI, and applications; generally, these are being innovated by both startups and existing cloud security platforms.
Again, cloud security vendors include hyperscalers (AWS, Microsoft, GCP), security companies (Palo Alto, CrowdStrike), and cloud security companies (Wiz, Orca).
4. Software Security - Protecting Software Development & Deployment

Secure software development has become increasingly important. Most security bugs are introduced in the coding phase, but not discovered until later on in testing or deployment. The later the bug is caught, the more expensive it will be to fix. Because of this, there’s been an increased focus on secure development which has led to the DevSecOPs term. This focuses on integrating secure practices into software development, instead of applying security features at the end of the process.
A cloud-native application protection platform (CNAPP) provides an integrated tool for monitoring, detecting, and acting on potential cloud security and application threats. Application security testing identifies security defects from code to deployment. Software supply chain is tied to these tools and focuses on securing/tracking the components involved in software development. This helps identify bugs and helps identify the source of bugs once a breach occurs faster.
API Security & Web Application Firewalls (WAF) are a few other key components of web app security. APIs provide a way for software to interact with each other, and API security focuses on preventing dangerous requests from those APIs. Web Application Firewalls act like other firewalls and block certain requests based on pre-defined rules.
The important takeaway for software security is that security bugs can be introduced at any stage of the development lifecycle, and companies should aim to minimize the number of bugs introduced and protect applications once they’re in production.
Several vendors do application protection including the hyperscalers, cloud security platforms, Synopsys, Snyk, Cloudflare, and others.
5. Data Security - Protecting Data
Cybersecurity, at its core, is about protecting data so data security goes on throughout the lifecycle of security. If we go back to the fundamentals, security is about prevention, detection, and response; data security should plan around all three.
Governance is the way to define how a company wants to manage data. It includes a security policy (what data is sensitive), classification (what data is important), cataloging (where data is), and resilience (how data will be recovered).
Discovery is about finding where data is, whether it be structured or unstructured. It also entails understanding how data moves through the network. Data loss prevention is a means of discovering data loss in real time.
Finally, several tools are used for protecting the data. Encryption is used to scramble the data in storage or transit. Key management protects the keys that unencrypt the data. Finally, access control (again) ensures the wrong people don’t access certain data.
6. Infrastructure Security - Protecting Data Centers & Physical Infrastructure
The last piece of the network to call out is securing the physical infrastructure such as IoT devices, data centers, and manufacturing plants. A common example of hardware security includes a hardware firewall or proxy server that scans incoming and outgoing traffic from a physical network for potential threats.
IoT security is an interesting one as it connects endpoint security, hardware security, and cloud security. Physical security also plays an important role in ensuring unauthorized users can’t get physical access to machines/servers.
7. Security Operations - Lifecycle Technologies

I’m using the term security operations loosely here; I’m including processes that go on throughout the security lifecycle. Generally, these are process tools aimed at the prevention, detection, or response of security incidents.
The underlying technology for these tools is databases with analytics tools built in for detecting anomalies. Tools like IT asset management track a company’s technology (devices, applications, services). Monitoring and observability take it a step further to understand the health of data/applications and understand why issues may occur.
SIEM tools (security information & event management) perform a similar task by consolidating a company’s security data and analyzing it for potential concerns. If there is a concern, the SIEM will initiate an alert. An XDR (extended detection and response) tool will then investigate (detect) the incident. Finally, a SOAR (security orchestration automation and response) tool will automate the response to a security incident.
Security processes are heavily scrutinized (by executives, regulators, and customers). When something goes wrong, people want to know why. Governance, risk, and compliance (GRC) tools provide one way to manage that. Finally, most of these services mentioned in the article can be outsourced to other companies, and services are one of the largest sub-industries in security.
Where Major Companies Fit into the Ecosystem
I’ll briefly touch on where some of the largest security companies in the world fit into the ecosystem. All of these companies offer products across the security ecosystem and strive to offer security platforms that customers can consolidate on.
Microsoft
In January 2021, Microsoft surpassed $10B in security revenue. Just two years later, Microsoft announced they passed $20B in revenue from Microsoft security.
Microsoft has 6 main segments of its cybersecurity portfolio: Microsoft Defender, Microsoft Sentinel, Microsoft Entra, Microsoft InTune, Microsoft Priva, and Microsoft Purview. Defender (cloud, apps, endpoint, IoT) is Microsoft’s security product across solution areas. Sentinel is a SIEM/SOAR solution. Entra is Microsoft’s IAM solution (and the market leader by market share). InTune is a unified endpoint management tool. Priva covers data privacy and compliance. Finally, Purview is a data governance tool.
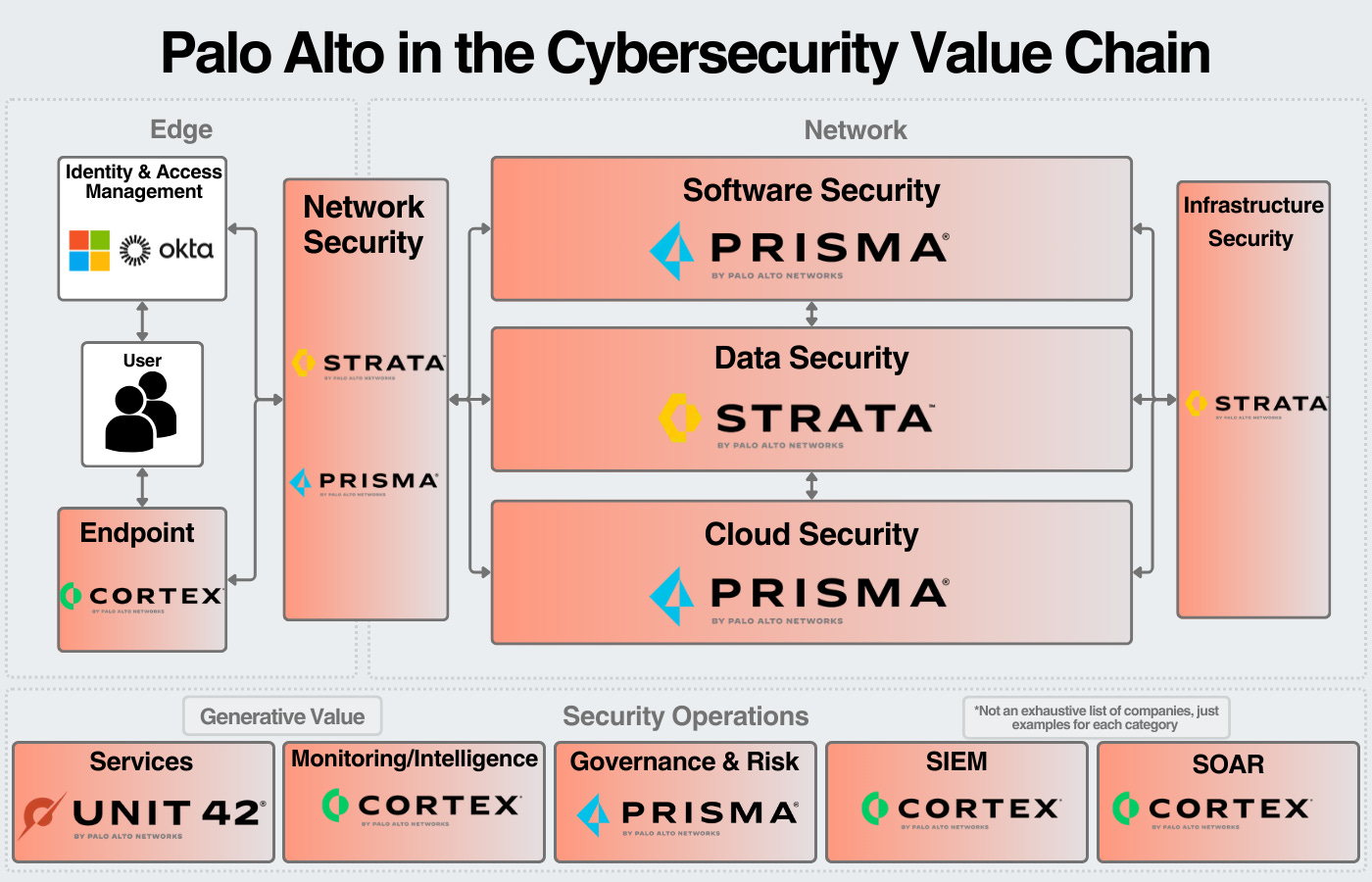
Palo Alto Networks
Palo Alto is the largest pure-play cybersecurity company in the world by both market cap and revenue. Their core product is network firewalls (hardware & software); through an aggressive acquisition strategy, they have significantly expanded their portfolio. Their goal is to be the consolidator across cybersecurity and they continue to show progress towards that goal.
Palo Alto has four main solution areas: Strata (Network), Prisma (Cloud, Access), Cortex (Endpoint, SecOps), and Unit 42 (Managed Services). The only area they don’t compete in is Identity. They’ve done $7.5B in revenue over the last 12 months.
CrowdStrike
Crowdstrike’s core product is in endpoint security; they’re another example of the ability to expand to a platform. In endpoint security, they are one of the two market leaders (Microsoft being the other). In cloud & software security, they have a unified platform for posture management, workload protection, and app protection. They offer a data protection suite as well as services across security operations. They don’t offer Identity & Access Management, but they do offer identity security protecting other IAM products.
Their product is built around a unified data layer. CEO George Kurtz explained the CrowdStrike platform here, explaining that the endpoint is just a delivery module. The real value comes from centralizing data, using AI/ML to detect threats and anomalies, and responding to those threats. That value can continually be delivered through new products which gives us the general roadmap of how CrowdStrike expands moving forward. CrowdStrike has done $2.8B in revenue over the last 12 months.
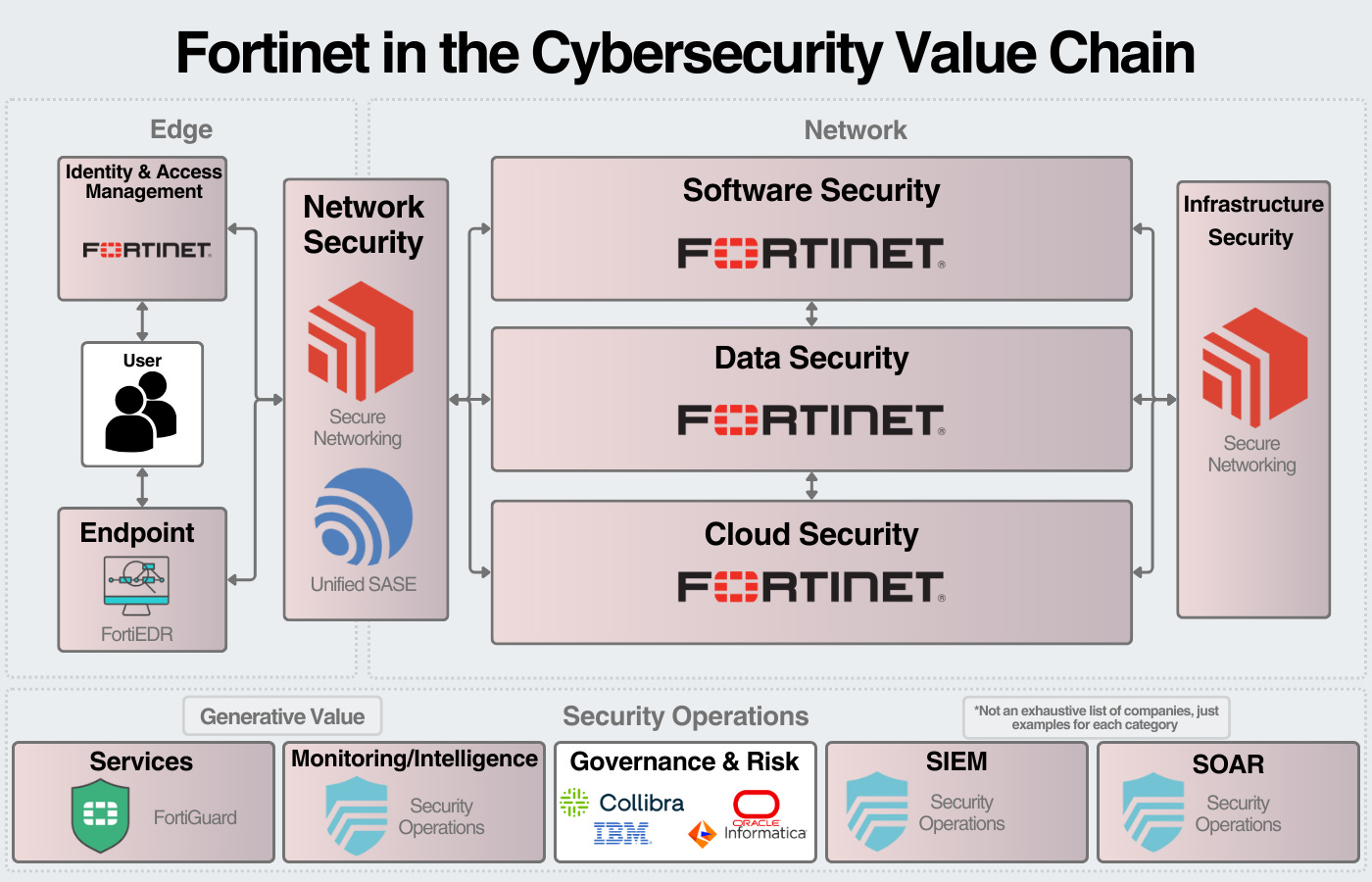
Fortinet
Fortinet is the 2nd largest pure-play cybersecurity company by revenue. Like Palo Alto, their core product is the firewall (both hardware & software). Fortinet is still primarily a networking security company (60-70% of revenue) and is focused on delivering a strong SASE product for growth. With that being said, they have an expansive portfolio of security products including cloud security, app security, data security, and managed services. Fortinet has $5.3B in revenue over the last 12 months.
Google
One of Google’s primary goals is to be the go-to cloud for security, and they’ve done an impressive job of building out their portfolio. They offer network security with load balancing, cloud firewalls, and secure web proxies. GCP offers several services for data protection (building on its strength as a data company). They also focus on securing DevOps as well with several SecDevOps tools.
In 2022, Google completed its acquisition of Mandiant for $5.4B, which bolstered GCP’s managed services offerings (in addition to other products). When combined with their data governance, observability, and SIEM/SOAR solution, it makes GCP a formidable player in the security space. It will be interesting if management discloses any revenue numbers for security in the future.
Cisco
Cisco has an impressive collection of security products; with its acquisition of Splunk, it will be one of the largest security companies in the world. In fiscal year 2023, Cisco brought in ~$4B in security revenue while Splunk had $3.7B in ARR at the end of the same quarter. Combined, this puts Cisco in the same revenue ballpark as Palo Alto.
Cisco’s core security strength comes from its massive networking business. They have expanded to cloud, endpoint, and SASE as well. Splunk brings a strong SecOps presence with SIEM, SOAR, and analytics. It will be interesting to see if Cisco can generate synergies between the two companies once Cisco’s acquisition of Splunk closes.
Overall, I think the cybersecurity landscape is fascinating. The cybersecurity industry has several intriguing investment characteristics: high demand, (seemingly) unlimited time horizon for growth, pricing power, and a massive TAM.
On the other hand, there’s an exceptional amount of competition, fragmentation, and the barrier to execution is high. The other concern is that big tech has such a dominant distribution network that maintaining growth rates and pricing power for smaller companies will be challenging.
Summarizing my thoughts: I’m confident in saying the cybersecurity industry will be significantly larger in a decade, but picking the companies that will outperform over the next decade is a challenging proposition.
As always, thanks for reading!
Disclaimer: The information contained in this article is not investment advice and should not be used as such. Investors should do their own due diligence before investing in any securities discussed in this article. While I strive for accuracy, I can’t guarantee the accuracy or reliability of this information. This article is based on my opinions and should be considered as such, not a point of fact. I’m a Microsoft employee, all information contained within is public information or my own opinion.









Thanks for sharing! Are there any resources / readings you’d recommend to better understand the space?
Great read, I would that security policies and standards underpin every cyber program. Policy drives the security strategy and standards the tactical delivery of control activities you talk about. Without these the cyber program would be directionless and ineffective.